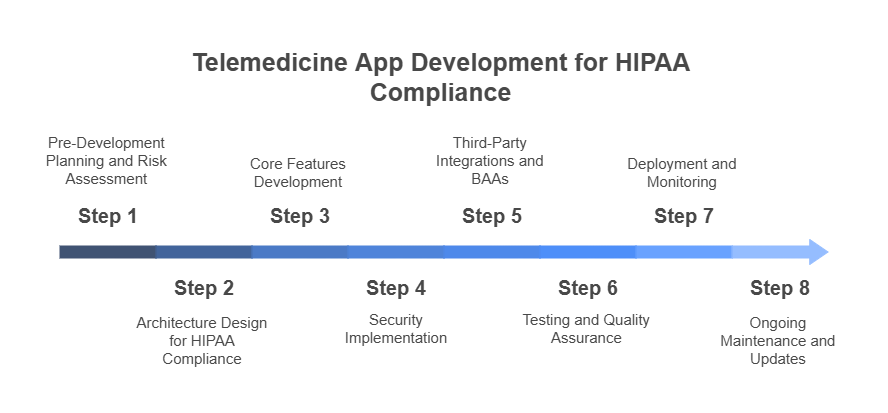
Steps to Build a HIPAA Compliant Telemedicine Appointment App: Complete Development Guide
14 Jun 25 


The telemedicine market reached $83.5 billion in 2024, but here’s the catch: 78% of healthcare apps fail HIPAA compliance audits within their first year. One violation can cost your business $50,000 to $1.5 million in fines.
Building a HIPAA compliant telemedicine app isn’t just about adding encryption. It requires understanding healthcare regulations, implementing proper security measures, and following strict development protocols from day one.
This guide walks you through every step of building a telemedicine appointment app that passes HIPAA audits and protects patient data while delivering exceptional user experience.
Understanding HIPAA Compliance Basics
HIPAA (Health Insurance Portability and Accountability Act) sets the standard for protecting sensitive patient information. Any app handling Protected Health Information (PHI) must comply with HIPAA rules.
What Qualifies as PHI:
- Patient names and contact information
- Medical records and treatment history
- Appointment schedules and doctor notes
- Payment information linked to medical services
- Any data that can identify a patient’s health status
HIPAA’s Three Main Rules:
- Privacy Rule: Controls how PHI is used and shared
- Security Rule: Sets technical safeguards for electronic PHI
- Breach Notification Rule: Requires reporting security incidents
Your telemedicine app becomes a “covered entity” under HIPAA when it stores, processes, or transmits PHI. This means you’re legally responsible for protecting this data according to federal standards.
Essential HIPAA Requirements for Telemedicine Apps
Administrative Safeguards
Your development team needs designated HIPAA compliance officers, security training programs, and documented policies for handling PHI. Every team member accessing patient data must complete HIPAA training and sign confidentiality agreements.
Physical Safeguards
Server locations, data centers, and development environments must meet HIPAA physical security standards. This includes restricted access, surveillance systems, and documented visitor logs.
Technical Safeguards
Your app must implement access controls, audit logging, data encryption, and secure transmission protocols. Every piece of PHI must be encrypted both at rest and in transit using AES-256 encryption or equivalent.
Step 1: Pre-Development Planning and Risk Assessment
Conduct a HIPAA Risk Assessment
Document every point where your app will handle PHI. Map data flows from patient registration through appointment scheduling to video consultations. Identify potential vulnerabilities and create mitigation strategies.
Key Questions to Answer:
- Where will PHI be stored?
- Who has access to patient data?
- How will data move between app components?
- What third-party services will process PHI?
- How will you handle data breaches?
Choose Your Development Approach
Native apps offer better security control but require separate iOS and Android development. Cross-platform frameworks like React Native or Flutter can work for HIPAA compliance if properly configured.
Select HIPAA-Compliant Infrastructure
Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform offer HIPAA-compliant hosting options. These providers will sign Business Associate Agreements (BAAs) and provide the necessary security controls.
Step 2: Architecture Design for HIPAA Compliance
Database Security Architecture
Use encrypted databases with field-level encryption for sensitive data. PostgreSQL and MongoDB offer HIPAA-compliant configurations when properly set up.
Database Security Requirements:
- Encrypted storage with AES-256
- Role-based access controls
- Audit logging for all database queries
- Regular security patches and updates
- Automated backup encryption
API Security Design
Your telemedicine app’s APIs must implement OAuth 2.0 or similar authentication protocols. Every API endpoint accessing PHI needs proper authorization checks.
API Security Checklist:
- JWT tokens with short expiration times
- Rate limiting to prevent abuse
- Input validation and sanitization
- HTTPS only for all communications
- API logging without exposing PHI
Data Flow Architecture
Design your data architecture to minimize PHI exposure. Use data segregation techniques to separate identifying information from medical data when possible.
Step 3: Core Features Development
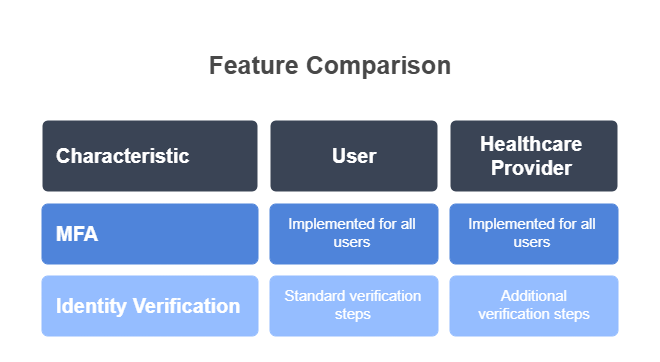
User Registration and Authentication
Implement multi-factor authentication (MFA) for all users. Healthcare providers should have additional verification steps beyond standard patients.
Registration Requirements:
- Strong password policies (minimum 8 characters, mixed case, numbers, symbols)
- Email or SMS verification
- Identity verification for healthcare providers
- Consent forms for data processing
- Terms of service acknowledgment
Appointment Scheduling System
Your scheduling system must prevent PHI exposure while allowing efficient appointment management.
Scheduling Features:
- Available time slot management
- Automated appointment reminders (without PHI in messages)
- Cancellation and rescheduling options
- Provider calendar integration
- Waiting room functionality
Video Consultation Platform
The video component requires end-to-end encryption and secure transmission protocols.
Video Platform Requirements:
- WebRTC for peer-to-peer communication
- STUN/TURN servers for connectivity
- Recording capabilities (if required)
- Screen sharing with PHI protection
- Chat functionality with encryption
Patient Health Records Integration
If your app accesses existing health records, implement HL7 FHIR standards for interoperability.
Integration Considerations:
- Electronic Health Record (EHR) connectivity
- Lab results display
- Prescription management
- Medical history access
- Care plan sharing
Step 4: Security Implementation
Data Encryption
Implement encryption at multiple levels: database encryption, file system encryption, and transmission encryption.
Encryption Standards:
- AES-256 for data at rest
- TLS 1.2 or higher for data in transit
- End-to-end encryption for video calls
- Key management using AWS KMS or similar
- Regular encryption key rotation
Access Control Systems
Design granular permission systems that follow the principle of least privilege.
Access Control Features:
- Role-based access control (RBAC)
- User session management
- Automatic session timeouts
- Device registration and management
- Login attempt monitoring
Audit Logging
Track all access to PHI with comprehensive audit logs that cannot be modified.
Logging Requirements:
- User authentication events
- PHI access and modifications
- System configuration changes
- Failed login attempts
- Data export activities
Step 5: Third-Party Integrations and BAAs
Business Associate Agreements
Any third-party service that processes PHI must sign a Business Associate Agreement. This includes cloud providers, payment processors, and analytics services.
Common Third-Party Services Requiring BAAs:
- Cloud hosting providers
- Email service providers
- SMS notification services
- Payment processing platforms
- Analytics and monitoring tools
Payment Processing Integration
Use HIPAA-compliant payment processors like Stripe (with BAA) or Square for Healthcare.
Payment Security Requirements:
- PCI DSS compliance for credit card processing
- Tokenization of payment information
- Separate payment data from medical records
- Encrypted transaction processing
- Fraud detection without PHI exposure
Notification Systems
Email and SMS notifications must exclude PHI while providing necessary appointment information.
Notification Best Practices:
- Generic appointment reminders without medical details
- Secure portal links for detailed information
- Patient preference management
- Opt-out capabilities
- Message delivery confirmation
Step 6: Testing and Quality Assurance
Security Testing
Conduct comprehensive security testing including penetration testing and vulnerability assessments.
Testing Requirements:
- Automated security scanning
- Manual penetration testing
- Code review for security vulnerabilities
- Database security assessment
- Network security validation
HIPAA Compliance Testing
Test your app against specific HIPAA requirements using compliance checklists and audit tools.
Compliance Testing Areas:
- Data encryption verification
- Access control validation
- Audit log functionality
- Backup and recovery procedures
- Incident response protocols
User Acceptance Testing
Include healthcare professionals in your testing process to ensure the app meets clinical workflow requirements.
Testing Scenarios:
- Patient registration and verification
- Appointment scheduling workflows
- Video consultation quality
- Emergency situation handling
- System performance under load
You may also read 5 Key Elements for Designing a User-Friendly Telemedicine App
Step 7: Deployment and Monitoring
Production Environment Setup
Configure your production environment with proper security controls and monitoring systems.
Production Requirements:
- Separate staging and production environments
- Database replication and backup systems
- Load balancing and failover capabilities
- Security monitoring and alerting
- Performance monitoring dashboards
Continuous Monitoring
Implement 24/7 monitoring for security incidents and system performance.
Monitoring Components:
- Intrusion detection systems
- Unusual access pattern alerts
- System performance metrics
- Database activity monitoring
- Network traffic analysis
Incident Response Planning
Develop and document procedures for handling security incidents and potential HIPAA breaches.
Incident Response Elements:
- Breach notification procedures
- Patient communication protocols
- Regulatory reporting requirements
- Evidence preservation methods
- Recovery and remediation steps
Step 8: Ongoing Maintenance and Updates
Security Updates
Establish procedures for applying security patches and updates without disrupting patient care.
Update Management:
- Regular security patch schedules
- Testing procedures for updates
- Rollback capabilities
- Change documentation
- User notification processes
Compliance Auditing
Schedule regular HIPAA compliance audits to identify and address potential issues.
Audit Activities:
- Annual risk assessments
- Quarterly security reviews
- Access control audits
- Policy and procedure updates
- Staff training verification
Technology Stack Recommendations
Backend Development
- Languages: Python (Django/Flask), Node.js, or Java
- Databases: PostgreSQL with encryption, MongoDB Atlas
- Cloud Platforms: AWS with HIPAA BAA, Microsoft Azure, Google Cloud
- Authentication: Auth0, AWS Cognito, or custom OAuth implementation
Frontend Development
- Mobile: React Native, Flutter, or native iOS/Android
- Web: React, Angular, or Vue.js with HTTPS enforcement
- Video: WebRTC, Agora.io, or Twilio Video API
Security Tools
- Encryption: AWS KMS, HashiCorp Vault
- Monitoring: Splunk, ELK Stack, or AWS CloudWatch
- Vulnerability Scanning: Veracode, Checkmarx, or OWASP ZAP
Cost Considerations for HIPAA Compliance
Development Costs
HIPAA-compliant development typically costs 30-40% more than standard app development due to additional security requirements and compliance measures.
Also read How is AI Utilized in Healthcare Apps?
Cost Factors:
- HIPAA compliance consulting: $15,000-$50,000
- Security infrastructure: $5,000-$20,000 monthly
- Third-party BAA services: $500-$5,000 monthly
- Compliance auditing: $10,000-$30,000 annually
- Legal and regulatory review: $10,000-$25,000
Ongoing Operational Costs
Factor in ongoing compliance costs including monitoring, auditing, and staff training.
Monthly Operational Expenses:
- HIPAA-compliant hosting: $1,000-$10,000
- Security monitoring tools: $500-$3,000
- Compliance management: $1,000-$5,000
- Insurance and liability coverage: $500-$2,000
Common Compliance Pitfalls to Avoid
Inadequate Documentation
Many apps fail audits due to poor documentation of security procedures and data handling practices. Document everything from the beginning.
Insufficient Access Controls
Overly broad user permissions create compliance risks. Implement granular access controls that follow the minimum necessary standard.
Weak Encryption Implementation
Using outdated encryption methods or improper key management leads to compliance failures. Stay current with encryption standards.
Third-Party Service Oversights
Failing to obtain proper BAAs from all service providers processing PHI creates significant compliance risks.
Inadequate Staff Training
HIPAA violations often result from employee errors. Implement comprehensive training programs and regular refresher courses.
Mindster’s Expertise in HIPAA-Compliant Telemedicine Development
Mindster brings deep expertise in developing HIPAA-compliant healthcare applications with a proven track record of successful telemedicine platform deployments. Our team understands the complex intersection of healthcare regulations, security requirements, and user experience design.
Our Telemedicine Development Services:
- Custom telemedicine app development for iOS and Android
- Web-based patient portals with video consultation capabilities
- EHR and practice management system integrations
- Real-time chat and messaging with PHI protection
- Appointment scheduling and automated reminder systems
- Secure payment processing and billing integration
Mindster’s development process includes HIPAA compliance from the initial planning stages through deployment and ongoing maintenance. We work closely with healthcare organizations to ensure their telemedicine solutions meet regulatory requirements while delivering exceptional patient and provider experiences.
Our compliance-first approach means your telemedicine app will pass HIPAA audits and provide the security foundation necessary for scaling your telehealth services.
Ready to Build Your HIPAA-Compliant Telemedicine App?
Don’t risk HIPAA violations or compliance failures. Partner with Mindster to develop a telemedicine appointment app that meets all regulatory requirements while delivering superior user experience.
Get Your Free HIPAA Compliance Assessment – Our healthcare app development experts will review your requirements and provide a detailed roadmap for building your compliant telemedicine solution.
Contact Mindster Today to discuss your telemedicine app development project and learn how we can help you navigate HIPAA compliance while building a successful healthcare platform.
Frequently Asked Questions
How to build a HIPAA compliant app?
Building a HIPAA compliant app requires implementing administrative, physical, and technical safeguards. Start with a risk assessment, use encrypted databases, implement proper access controls, ensure all third-party services sign BAAs, and maintain comprehensive audit logs. Every component must be designed with PHI protection in mind.
How to develop a telemedicine app?
Telemedicine app development involves user registration systems, appointment scheduling, secure video consultation platforms, and patient record integration. Focus on user experience for both patients and healthcare providers while ensuring HIPAA compliance, implementing end-to-end encryption, and integrating with existing healthcare systems.
How to make something HIPAA compliant?
To make any system HIPAA compliant, conduct a thorough risk assessment, implement required safeguards (administrative, physical, and technical), encrypt all PHI, establish access controls, create audit logging, obtain BAAs from vendors, train staff, and develop incident response procedures. Regular compliance audits ensure ongoing adherence.
How do I make sure my software is HIPAA compliant?
Ensure software HIPAA compliance by implementing AES-256 encryption, role-based access controls, comprehensive audit logging, secure authentication, and proper data backup procedures. Regular security testing, vulnerability assessments, and compliance audits verify ongoing adherence to HIPAA requirements.
Can an app be HIPAA compliant?
Yes, apps can be HIPAA compliant when properly designed and implemented. Mobile and web applications handling PHI must follow the same HIPAA requirements as any healthcare system, including encryption, access controls, audit logging, and administrative safeguards. Many successful healthcare apps maintain full HIPAA compliance.
How do I create a healthcare app?
Creating a healthcare app requires understanding regulatory requirements (HIPAA for US), choosing appropriate technology stacks, implementing security measures, designing user-friendly interfaces for patients and providers, integrating with existing healthcare systems, and ensuring compliance through testing and auditing. Consider partnering with experienced healthcare app developers.
How do I make my Zoom account HIPAA compliant?
To make Zoom HIPAA compliant, upgrade to Zoom for Healthcare, sign a Business Associate Agreement with Zoom, enable end-to-end encryption, disable cloud recording (or ensure encrypted storage), restrict meeting access, and train staff on compliant usage. Standard Zoom accounts are not HIPAA compliant.
Is API HIPAA compliant?
APIs can be HIPAA compliant when properly secured with OAuth authentication, TLS encryption, input validation, rate limiting, and comprehensive logging. The API provider must sign a BAA if processing PHI. Ensure all data transmission and storage meets HIPAA technical safeguards, and implement proper access controls for API endpoints.
- Agentic AI1
- Android Development3
- Artificial Intelligence38
- Autopay1
- Classified App3
- Custom App Development5
- Digital Transformation12
- Doctor Appointment Booking App14
- Dropshipping1
- Ecommerce Apps40
- Education Apps2
- Fintech-Apps38
- Fitness App4
- Flutter4
- Flutter Apps20
- Food Delivery App5
- Grocery App Development1
- Grocery Apps3
- Health Care10
- IoT2
- Loyalty Programs11
- Matrimony Apps1
- Microsoft1
- Mobile App Maintenance2
- Mobile Apps134
- On Demand Marketplace1
- Product Engineering6
- Progressive Web Apps1
- React Native Apps2
- Saas Application2
- Shopify9
- Software Development3
- Taxi Booking Apps7
- Truck Booking App5
- UI UX Design8
- Uncategorized7
- Web App Development1



















Comments